
A biometric technology system that uses facial recognition features that can distinguish and identify a person. One of the main advantages of this system is to assist law enforcement for the protection of safety and security.
Data Lookup Visual

Image Verification
Face match process verifies the object if two faces belong to the same person.
Analog to Digital Transformation
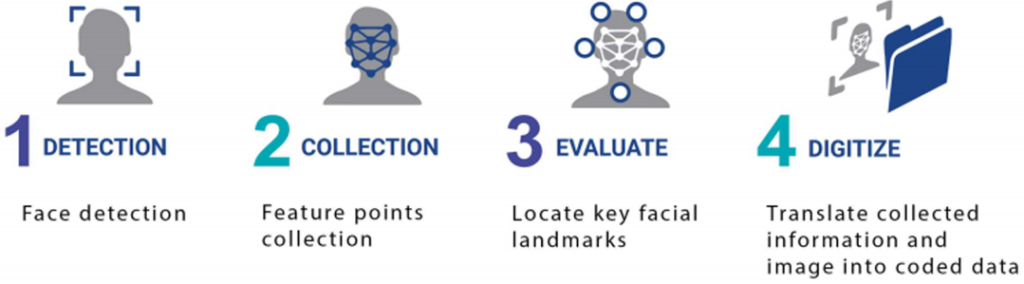
Face capture process transforms analog information (a face) into a set of digital information (data or vectors) based on the person’s facial features.
Facial Recognition
Face detection process is and essential step in detecting and locating human faces based on images dataset.

About
System Algorithm
Face recognition systems use computer algorithms to pick out specific, distinctive details about a person’s face. These details, such as distance between the eyes or shape of the chin, are then converted into a mathematical representation and compared to data on other faces collected in a face recognition database. The data about a particular face is often called a face template and is distinct from a photograph because it’s designed to only include certain details that can be used to distinguish one face from another.
Features
What We Offer
Our technologies has a several feature that could help investigator to speed up their investigations cases.
Easy to Deploy
The system solutions is easy to deploy since our framework using commonly available operating systems.

Easy to Enhance
The system solution is easy to be enhanced in terms of capacity, speed and system capability, if in the future it is needed to expand the ability to serve a wider demand.
Multiple Access
The system solution is built and designed according to the customer needed which required simultaneous access at the same time.
Public Networks
The system is designed to be able to communicate or connect by utilizing the public internet network that is configured securely and specifically.
Security
The system is built using leveling access control, thus limiting access to the system directly without passing through the selection protocol.